Coffee Break 2025.27.10
Half-caf and planning for the week…
Happy Monday humans,
The government shutdown canceled my drill weekend for the National Guard, so I found myself with extra time on my hands… most of which I used to sleep and get over a cold. 😴 I’m nursing a phlegmy throat and a cup of half-caf this morning as I layout my plans for this mornings study session, the shifts I hope to pick up for work later in the week, and the travel plans I have for next weekend.
Last week we saw the severe amazon AWS outage disrupt a massive array of businesses and services. Personally, I was unaffected. How about you?
It goes to show how much we over-rely on digital infrastructure to keep our economy functioning. Incidents like this are, I hope, a bit of a wake-up call to businesses and services that the strength of the internet is its decentralization. If we give up that decentralization and focus everyone’s service through the same, almost monopolistic infrastructure with no fail-overs, we’ll be up a creek every time some junior engineer typos during DNS configuration.
Coffee Break // Cyber News 014
Weekend news round-up! How safe is our critical infrastructure from foreign cyberattack?
Happy Monday, y’all!
In the news this past weekend I see the South Korean government is making what sounds to be pretty slow progress on restoring their destroyed data center. At only 36.7% recovered at the time that article was posted, I suspect that incremental progress will continue towards, but never reach, 100% for them.
Over my coffee this morning I read CBS News’ interview with Retired General Tim Haugh. In it, he interprets China’s aggressive targeting of our critical infrastructure over the past several years through the lens of war-preparation. In his view, there is no other economic or social motivation for such attacks.
When considering the silent cyber war with China, I reflect with some trepidation on the divided nature of our internal politics right now. One of the few advantages of the totalitarian Chinese system is that they present a comparatively unified force. Right now in the USA we are perilously divided. If we were thrown into a war tomorrow, how would we handle the long-term resource cost, especially if our enemies can remotely attack so much of our infrastructure? Would a fractured nation like ours really be able to rally together to support a conventional war effort?
And, if we’re going beyond cyber warfare in our considerations, what is being done about Chinese farmland ownership? Even if we pass laws like many states have to prevent foreign ownership of property near military bases, how are we going to vet and prevent our enemies overseas from utilizing shell companies?
Finally, a developing story that I’m beginning to follow is the firing of California Cybersecurity Chief Edward Bombita. This one could end being a nothing burger or an HR complaint, but mid-high profile firings without cause always beg the question: what don’t they want the public to know?
Coffee Break // Cyber News 013
Happy Friday. The South Korean government slowly rebuilds its data-center, and a bill to protect our own supply chain sits in limbo in the House…
A hot cup of decaf again today. The taste of a hot beverage helps me slide into the second half of the day, even without the caffeine.
D’you know what’s a funny word? Timestomping. Easily misread as timestamping, timestomping is when a threat actor alters the timestamps in logs/files in order to hide evidence of their activity, or help their malicious files blend in with legitimate data. What a fun bit of trivia… Happy Friday everyone.
//
In the news.
The online services damaged by the data-center fire in South Korea are slowly but surely being restored. The Korea Herald reports that 30% of the services the data-center supported are back online.
I want to draw a thematic link between that data-center fire and this op-ed on the criticality of our own supply chain. In it, Lt. Col. Jesse R. Humpal expresses his support for a supply chain bill that he argues will help dedicate resources to protecting our supply chain.
I personally don’t know enough about the legislation itself to say whether or not it is a good idea, but he makes a strong argument. His best line is drawn from another article from the same publication:
“The Pentagon’s arsenal and defense industrial base is built on materials that China can turn off like a light switch.”
In other news, a story from earlier in the week on a novel surveillance method: using a person’s mouse as a microphone. The project, nicknamed Mic-E-Mouse by the researchers developing it, uses the mouse’s polling data in conjunction with a neural network to (somewhat) accurately derive conversations and sound from the surrounding space.
This is pretty cool, but it’s worth mentioning that using light to pick up sound is a technique that goes all the way back to the KGB in the 1940s.
Coffee Break // Cyber News 012
A data center in South Korea burns to the ground. Was it arson or poor planning? Also, some thoughts about FISA and digital surveillance here at home.
I’m comforting myself with a hot cup of a medium roast Dunkin’ brand coffee this evening. I’m reading an excellent Op-Ed in the Hill by Ron Yokubaitis, a name in the ISP and data game, on the matter of surveillance.
“This is not a partisan issue. It’s a constitutional issue. The Fourth Amendment doesn’t say “except when it’s digital.” It doesn’t say “unless you’re using Google.” It says the government must get a warrant — period.”
—Ron Yokubaitis
I recommend the whole article to all interested parties. I heartily concur with Yokubaitis’ take. To give a fair airing to the other side of the argument, however, it should be noted that some would view Internet traffic and data more akin to conversations in public spaces. The argument goes something like this: “You have no expectation of privacy in a public forum such as at the mall or a restaurant, why would you have that expectation in the virtual forum of the internet?”
I would argue here, that certain forums on the internet absolutely fall into the category of a public forum, but we should not conflate reasonable expectations with constitutional rights here. At this point in time, I think it’s reasonable to assume everything you see, say, and do online is fully recorded and documented in some form, even if it is a form that will not be successfully decrypted before quantum computing comes to the fore. However, even without an expectation that your digital footprint is private, you still (largely speaking) have the right to defend it as such. Just because someone may come along and compromise the security of your communications does not mean that anyone else would have a right to view them as well.
If a lunatic took my door off it’s hinges, would that give my neighbor the right to walk inside and go through my things?
How do you treat your online communications? Does the potential for a omniscient Singularity in the near-future influence your choices?
//
In the news.
Keyboard Transport Layer Security offers a potential defense against Keyloggers on computers with Intel TPMs or perhaps some equivalent in the future.
A keylogger is a piece of hardware or software that sits in-between a Human Input Devide (HID) like a keyboard and the computer it’s sending that input to, and recording those inputs before they get to the computer. This way, attackers can catch important keystrokes (such as usernames and passwords) without the having to deal with encryption or hashes of any kind.
The KTLS described in the link above provides a means of encrypting those keystrokes so that even if a hacker is able to get their hands on the input data being passed through, it will not be readable or usable.
Back-ups, back-ups, back-ups. A story that went under the radar for many of us last week, was the a devastating data center fire in South Korea last week. The fire destroyed 858 TB of data and, crucially, also destroyed the back-ups which were being stored at the same location.
While geographic dispersion may not be critical for your home network and family photos, for a data center that stores a government agencies records, having back-ups at geographically separated sites is not merely recommended, it’s critical.
While luckily no-one died in the fire itself, a number of individuals have been arrested by officials on suspicion of criminal involvement and a government worker overseeing the network restoration has apparently taken his own life.
While this fire could very well be an unfortunate accident, one can easily see a target like this as being of interest to a foreign power. I don’t see any evidence of nation-state actors at this time, but the arrests indicate that there may well be something go on here that the South Korean government is not telling the public.
Coffee Break // Home Pen-Testing 001 // Cyber News 011
My experiments with pen-testing my home network continue… what is Cameradar? Can I use it to gain access to things I shouldn’t?
A café lungo with a few ounces of half-caf is my brew today. The flavor lacks a bit of body, but it came out nice and foamy which (if I’m being honest) was my main goal in combining the two.
//
Pen-testing progress.
Last night I had a couple of hours to spend more time learning pen-testing techniques with my authorized attempts to gain access to my family’s security system.
I had left off having determined that at least some of the security devices in question were accessible via the local network.
I spent some time doing a bit of research on the manufacturer of those devices in question, and performed a more detailed network scan of the specific IP address that was related to that company.
At this point in time, I was fairly certain that the device in question was a Network Video Recorder, the brains of the camera system and the place where all of the footage was being recorded to an SSD or HDD. I learned that most models of NVR from this manufacturer are designed to stream their video to a paired app over Wi-Fi.
Now that I know what I’m looking for… how do I get access to it?
I installed and toyed with the app in question for a few minutes, but quickly determined that there wasn’t really anything I could licitly do with it—after all, the manufacturer of the security cameras was not a participant in this pen-test.
If I was an actual attacker, I probably wouldn’t hesitate to set up an account with the app and see if I could brute force the username/password combination, or experiment with trying to capture the hash of an accounts password over the network.
However, I felt that anything that could potentially interact with the manufacturer’s servers would be unethical: while I feel perfectly comfortable searching for vulnerabilities in the products that my family owns and has authorized me to test, I have no authorization from the manufacturers of those products to test the security of their user account system or server infrastructure. I’m pen-testing my network; not theirs.
Since that attack vector was off the table, I uninstalled the app and returned my focus to the local network. Scanning the target IP with nmap again, I determined that it did in face have an open port that was configured to stream video from the cameras.
Ok, we’re back in the game. How do we gain access to that stream?
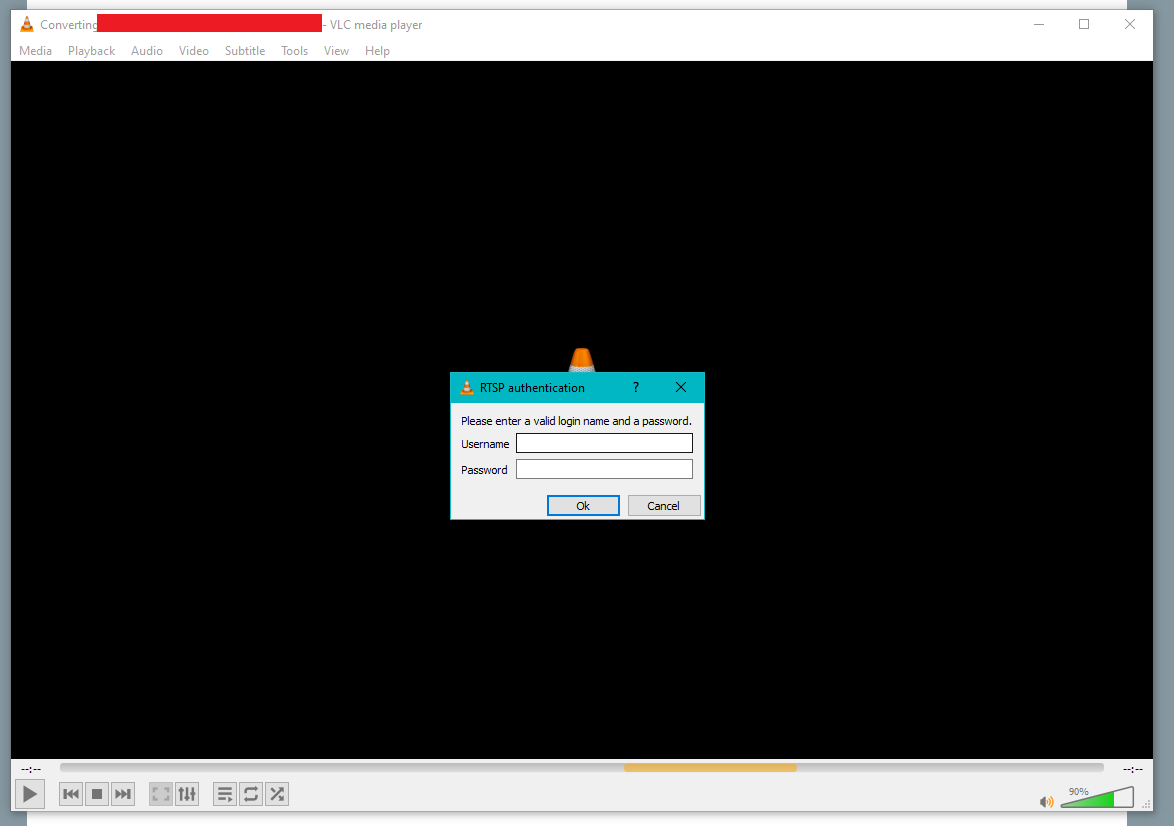
Many media players, like the popular VLC media player allow users to control video streams and save them as files, or stream them straight to the application. If I could find the MRL (think like a web address) of the stream, I could potentially get that video sent to VLC player on my computer.
But how to find the MRL? Enter Cameradar. A CLI tool built specifically for that purpose. Cameradar scans the target IP range for video surveillance cameras, and tries a library of default credentials and MRL/URL variations to find the camera’s log-on information and stream MRL.
With the NVR’s stream MRL in hand, I plugged it into VLC Media player… but there was an issue:
The stream was password protected. I mentioned Cameradar could attempt to crack username/passwords—this is true, but it does not come with an extensive dictionary or username/password combinations to try. Maybe 12 dozen at most.
Still that might have been enough to gain access here, except for one key detail that I’m aware of:
This NVR is not using default credentials.
For my pen-test this is a roadblock, but for the security of my family’s network, this is excellent. One of the most commonly overlooked vulnerabilities when laymen set up their home networks is a failure to change default credentials. Here my family has been smart enough to change their credentials away from easily guessable defaults.
I may still be able to break into this stream with a good script for a dictionary attack, but for the moment at least my efforts are thwarted.
Next time I come back to this project, I’ll research a few more ways to try and exploit the stream, and then turn my attention to the other unsecured devices on the network—even if they aren’t something I can leverage to compromise the vulnerability of the whole network, I can at least harden them specifically against attack.
//
In the news.
Something I want to discuss from earlier in the week, is the debates surrounding ICE reporting apps. Apple and Google have come under some degree of fire for complying with government requests to remove apps like ICEBlock, an app for alerting other users of local sightings of ICE employees and operations.
The governments argument is that apps dedicated to that purpose have the potential to promote violence against federal employees and facilitate attacks against them. There may be some truth to that, but some are questioning if this is an exaggeration or double-standard..
After all, other apps (including Google’s own Google Maps) include the ability to report LE speed traps and so forth.
Should those apps also be taken down, or have those features removed? Or is it ethically legal and acceptable to alert other people to the presence of LE officials.
Now there can be no doubt that Apple and Google have every right to remove content from their store fronts if they deem it potentially hazardous or problematic in any way. Even if they apply a double standard to their content, I think that’s there right.
Still, I feel like this story brings up some downstream questions. What will happen if the next time an administration demands Google and Apple to take down an app, they refuse?
Coffee Break // Home Pen-testing 000 // Cyber News 010
The start of my home security pen-test.
I’m enjoying a café lungo this morning, with a slight breakfast of some toaster naan. Delicious—would that all the calories I eat in a day could be so toasty and savory.
The coffee is gone altogether to quickly… I consider another, but I should make myself some real food instead.
But first, let me share with you some details of a pet-project that I’m working on…
//
Penetration testing. (it sounds dirtier than it is)
Yesterday evening I spent around two hours setting up a penetration test of my family’s home security network. For those that don’t know, a penetration test is a legal, authorized attempt to compromise security frameworks in order to strengthen them.
Imagine if you put new locks on your doors, then challenged a lock-picking enthusiast to try and break in. If he’s able to get past the locks, or otherwise gain unauthorized access within the parameters you define, then you learn valuable information about where the vulnerabilities in your attack surface are, and how to mitigate or avoid that risk in the future.
Ok, that’s great, but how do we go about testing the security system in my family’s home?
First we define our objective. My goal is simple:
To gain remote access to the security cameras in the house, learning the administrator password or otherwise compromising the system by non-physical means.
Why non-physical attacks? A physical attack on the system is outside of the scope for this pen-test. I live inside the house in question—I’m literally inside of the system already.
What could I learn by walking across the house and unplugging the recorder? Nada.
So instead, we’ll see what we can leverage across the network. First stop: reconnaissance.
I boot up Virtual box. It’s a software for running emulations of computers and their operating systems. A computer inside of a computer…
Within virtual box, I boot up a Kali Linux image. This is a Linux distribution that comes preloaded with security and pen-testing tools, like Zenmap, the program you see here on the left.
On the right is Wireshark’s OUI look-up tool. More on that in a bit...
I boot up Kali Linux is because I don’t have many pen-testing tools installed directly on my Windows PC. Luckily, Kali Linux is chock full of them.
One of the tools I’m interested in trying out at this stage is Zenmap. Zenmap is a user interface for nmap, the command line port scanning and network mapping tool.
With Zenmap I make a list of IP addresses active on the network, and several open ports on these computers. TCP/UDP ports are like channels you can exchange information over the network with. Open ports are necessary for using the internet or your home network, but certain ports run more secure protocols than others, so leaving specific ports open potentially leaves your computer vulnerable to attack.
Think about if you locked all your doors, but forgot to lock your windows! All a burglar would need is a ladder and BAM he’s in.
After scanning the network with Zenmap for a while, I take note of a few vulnerable ports on one of the IP addresses I discovered. I’ll set that aside for now; I’m really only interested in mapping the network at the moment.
I want to find my target. To do that I need to look at the IP and MAC addresses of the devices on the system.
So, as it turns out, I don’t need really need Zenmap just yet. Just a terminal Window and Wirehsark’s OUI look-up tool will do.
Switching back to my main Window’s machine, I run an arp command to learn which IP and MAC addresses are associated on the network.
With that information in hand, it’s a simple matter to run each MAC address through Wireshark’s OUI lookup tool and identify the manufacturer for each device.
Conveniently for me, only one of them is associated with home security equipment.
Excellent; target acquired.
Unfortunately this was all the time I had for this project on Monday, but my next steps are clear: research the target device and probe it for any vulnerabilities.
I’ll post an update on this when I have time to progress the project later.
//
In the news.
In one week, the EU will vote on a proposed law that would enable governmental oversight of all communications on apps like Signal, basically bypassing the privacy guarantees of end-to-end encrypted services.
Signal indicates that it will not offer its services in Europe if the law changes. Speaking of Signal, the privacy leader is adding new encryption to it’s system that it says will be future-proofed against the rise of quantum computing. While that claim is untested, I think it’s good that companies are continuously investing in better and better encryption methods.
Since encryption stops an attacker from reading intercepted data, but not from recording it, advances in computation like quantum computing theoretically present a future vulnerability, where attackers will eventually be able to decrypt communications they captured but were unable to crack years ago.
Do you use Signal or other encrypted apps? Do you trust the end-to-end encryption they advertise?
In other news, I was mildly disappointed to see that popular communications and social forum app Discord (my go to for communicating with friends about hobbies) announced it had suffered a data breach through it’s customer support platform.
Evidently the stolen in formation included names/usernames, email and contact information, billing information, and message history with customer service agents.
Worryingly for those that reached out to Discord to settle age-verification issues, the government issued-ID they used to verify their accounts were also compromised.
I use Discord a lot in my day-to-day—it’s an important (albeit unsurprising) reminder that data breaches occur all the time, and if you had your information included in a breach yet, you likely will at some point.
It just goes to show, if you don’t want to risk information being leaked, don’t keep it in a digital format at all.
Coffee Break // Cyber News 009
Happy Monday. How’s the surveillance weather by you?
Good morning folks,
Happy Monday. I’m enjoying a cup of Columbian espresso as I filter through the weekend’s cybersecurity news. The government shutdown here in America continue to drags on and, like every government shutdown, it hasn’t really effected me in any way. Although, I am forced to muse, it could delay my payments from the National Guard. Hm. It feels weird to be even technically a government employee.
//
Weekend news roundup.
CISA expired last week, arguably weakening our nation’s cybersecurity posture by reducing the ability of private sector actors to share threat information with each other without liability. This, in turn, encourages foreign threat actors, like Salt Typhoon and other state-sponsored APTs to dig deeper into our networks and infrastructure.
Oversees, privacy rights continue to erode even faster than in the US as Hong Kong is on track to have real-time facial recognition features in it’s ever-growing base of surveillance cameras. More concerningly to the west, the UK continues to force those same measures down their citizens’ throats, and despite assurances that they only use such technologies to catch serious offenders, mounting evidence to the contrary indicates that the UK government will happily use every possible technology to prosecute even the most milquetoast of offenders, and never mind the innocent people caught up in the tech’s false positives.
But as we know, US soil is hardly free of its own privacy encroachments. Business is booming for child surveillance tools at work in many US schools. But ignoring the huge false positive rates and unreliability of many of their threat detection systems, hidden cameras in smoke detectors, changing rooms and bathrooms:
“Surveillance doesn’t create safety; it creates fear, mistrust, and a chilling effect on student life.”
—Jon McCray Jones, Policy Analyst
Coffee Break // Cyber News 008
The Radiant hacker group has a change of heart? ICE purchases more cybertools…
I started my day today with a little hands-on work setting up a Raspberry Pi 5. A tiny prebuilt computer, I’ve hooked it up by the main wifi router with plans to turn it into a homeserver for some personal projects in the near future.
My coffee this morning is a pleasant shot of espresso. A Columbian grind, I think this may be favorite of the Nespresso varieties that I have tried.
Happy Friday, everyonel.
//
In the news.
CISA, the Cybersecurity Information Sharing Act (not to be confused with CISA) expired at the end of this September, ending liability and anti-trust protections for companies sharing cyber threat data with each other.
Threat sharing is one of the main ways that companies and governmental organizations stay safe from hackers and data-breaches, and the sunsetting of this legislation potentially chills important communication between parties in the cybersecurity space.
The blocking of CISA’s reauthorization is largely due to Sen. Rand Paul’s efforts to include new language in the act. MSSP Alert has the full story.
In a follow-up to the Kido nursery hack story from Tuesday, Radiant, the hacker group behind the breach, have allegedly caved to public backlash.
Originally fixed to a bitcoin ransom equal to around $808,000, the hackers have apologized for their actions targeting children and their families and (if you believe them) deleted all data from the hack.
ICE continues to turn heads in the Cybersecurity world as it continues to adopt and use powerful tools like PenLink.
At the core of the ethics debate surrounding tools like this is the question of warrantless searches. So much of the data that LE scrapes to use in tools like this comes purchased from data brokers.
Is it ethical for the government to amass huge volumes of personal and geographical data without warrants in this way? Do you think that the law has not kept up with the technology?
Coffee Break // Cyber News 007
Who would you trust with the power of Big Brother?
For my coffee this morning I pour myself a Red Eye… caffeine is the name of the game today.
I want to talk about the s-word:
Surveillance.
Anyone whose had the (dis)pleasure of speaking to me for more than a handful of minutes has probably heard me wax eloquent on the matter of state surveillance.
It would be tempting to think, then, that I’m opposed to concept en bloc.
Not at all—surveillance is an incredibly useful tool, it also just so happens to be one that is incredibly easy to abuse.
One doesn’t have to go far to find examples of useful surveillance. But as easy to find are examples of governmental overreach.
The UK Home Office has frequently pushed Apple (an industry leader in message privacy and encryption) to backdoor their data and provide data to them from users of any national origin.
And while the freedom loving patriot inside of all of us no doubt rebels at this attempted offense, we need to acknowledge the utility of these tools.
Consider the graph above… it seems pretty subjective, right? One of the hardest part of this debate is finding where to draw the line.
Everyone is ok with a bank having a security camera to safeguard their money, no one is ok with being videotaped in the shower.
I’m not qualified enough to create exact measurements for this hypothetical formula, but I can recommend a guideline for judging how “good” a tool may be.
How severely could a Nazi abuse it?
I’m thoroughly opposed to watering down the political discourse by name-calling members of either party, so if you think I’m implying anything about a particular faction at this time, you are mistaken.
No, what I want to do with this cartoonish example is remove the “it’s ok we’re the good guys” from your mind.
Forget how upstanding a person your local LE and Sheriff’s dept. might be, forget how patriotic and noble your friends and family in the military might seem.
When you are evaluating a technology or methodology, you need to imagine a devil at the helm, not an angel.
Picture a literal Nazi, a goose stepping SS member from 1939 with the skull on his hat and everything, and imagine what he would do with a given technology.
How about Flock cameras? A hugely popular pick among townships and cities across the US, Flock cameras and license plate readers have come under fire for being made widely available to all manner of agencies not originally contracted with them. (e.g. ICE, FBI, and more.)
My own neighborhood went to the trouble of installing cameras at the entrances to the development.
Flock provides some very real utility to LE. Last year I rode along with a local Sheriff’s deputy and saw firsthand how the deputies would get notifications if a license plate registered to a stolen car passed a given camera.
That’s pretty useful!
But let’s not forget our mental exercise. What if, instead of a honest, community focused sheriff’s deputy looking at that data, it was someone evil?
All of a sudden, I’m not so game to have free access to camera’s right by my house at every hour of the day.
Neither you nor I can pick who in government is going to have access to those systems. If we want to protect our 4th amendment rights, we have to limit the powers of the organizations that we fund through our tax dollars.
Every government and enforcement agency on Earth is pushing to equip themselves with the most advanced, AI-empowered surveillance systems in the world. It is in their interest to do so.
At the voting booth, it is your duty to tell them to restrain themselves for the good of our Republic and the morality of our culture.
//
In other news.
Security Week reports on an amusingly named attack procedure, the Battering RAM. The attack involves putting a piece of hardware, here called an interloper, between a computers CPU and DRAM memory. The device than can bypass protected memory addresses and encryption.
The good news? Someone would need to physically install the device for the attack to work. The bad news? It’s relatively cheap and easy to do so. Be careful leaving your computer with that shady computer repair shop!
China is tightening regulations for its service providers. Starting in November service providers will have only 60 minutes to report security incidents involving critical networks.
Reporting time limits are important for good response time in any jurisdiction, but 60 minutes is an insanely small window to hit. Fascinating.
Finally, an update on the NYC SIM farm. Jeffrey Burt of Security Boulevard reports that LE has found another 200,000 SIM cards and servers. Does this increased capacity lend greater credence to the Secret Service’s previous descriptions of the scale of the operation?
Coffee Break // Cyber News 006
A report on my day studying for the Sec+ exam.
It’s been a slow start to my day, I confess.
Awaking with a head-ache (Don’t stay up past midnight, kids) I enjoyed a lemon-lime Gatorade before my coffee today… meandering through my emails and a handful of communications left over from the day before, I turned at last to blessed caffeine.
Today I’m enjoying a Nespresso Capriccio. Nespresso encourages consumers to let this capsules “light acidity and a savory cereal note surprise you in this refreshing but deep light-roasted Arabica-Robusta espresso blend.”
Between you and me, I think it tastes like every espresso I’ve ever tried. Which, to be fair, is good.
After coffee, I adjust the parameters of Cold Turkey, an application and URL blocker that I use to stay focused on my work. Only the good lord knows why it took me this long to realize I could both block YouTube, and exempt specific educational channels in the same rule.
Confidently assured of my productivity, I spend too much time calibrating my AutoHotKey macros. I obsess over every keystroke saved by these trivial optimizations…
Practicing for the Sec+ Exam…
After breakfast/lunch, I consume a cup of half-caf and attempt a 90-minute practice exam from Professor Messer’s set. I just can’t quite come to the surface today… 80% correct, right on the line again.
The topics that threw me off all come from the sections on Security Architecture and Operations, with a few oddball questions about Encryption that I wasn’t sure about. It’s always nice to be able to see where you went wrong, and where you need to study up.
//
In the news.
I didn’t have much brain-power for the news today, but I did want to highlight a story from last week: a class action lawsuit against major credit reporting agency TransUnion. The TL;DR here is that TransUnion did not delete consumer data from its databases. This is an extremely common violation of consumers data rights—my gut instinct is that most companies don’t properly delete data they no longer should have because it is a) hard to enforce and b) they often have a financial incentive to continue leveraging that data.
In the case of credit reporting agencies like TransUnion, any user data is a data they can potentially sell to anyone who wants to evaluate a lendee’s likelihood of repayment.
How does it make you feel that credit reporting agencies are selling you as a product even when they shouldn’t?
Coffee Break // Cyber News 005
Surveillance, surveillance, surveillance…
Ah, surveillance, surveillance, surveillance. That double-edged sword… we love it when it’s used on the bad guys, we hate it when it’s used against us. I strike a contemplative pose as I put my cup of half-caf in the microwave to reheat, for no other reason than to pretentiously retell the moment here.
Surveillance, surveillance, surveillance… hm.
One of my biggest concern in this field is the massively growing capabilities of governmental agencies. People of all creeds have joked anecdotally about the NSA’s omniscience for years, but increasingly we see ICE and local LE openly gearing up with capabilities that rival the conspiratorial.
Reason.com details ICE’s 2 million dollar contract with Paragon, a remote phone hacking service, and their $11 million contract for Cellebrite devices to crack phones in their possession.
Further, reason reports that ICE has been accessing Flock security camera’s around the company without giving specific reasons, and Palantir was scheduled to deliver a prototype tracking system called ImmigrationOS.
It’s easy to distance ourselves from these issues by saying “that’s for illegal immigrants,” or “that’s just for criminals.” Remember, surveillance is a sword; it’s a weapon. If it’s used for good, it has it’s uses, but who oversees the ethics of its execution? Who ensures it won’t be used to silence political critics and viewpoints that whichever administration is in power want silenced? Make no mistake—left, right, foreign, or domestic, any party with power will abuse it. Don’t make the mistake of thinking the “good guys” have the power.
When evaluating any powerful weapon you must ask. How would I feel if this were in the hands of my enemy? Of people who hate me and mine?
I’d better finish this coffee before it’s cold again.
\\
Also in the news.
The internet runs on encryption. In the big bowl of wifi and cell signals, the only thing keeping your information from being exploited by threat actors is its secrecy. But all that could change if the quantum computing arms race comes to fruition. A story from CIO details how current encryption standards are maybe not prepared for the paradigm shift that quantum computing could potentially bring. Although, cracking AES-256 is estimated to take trillions of years with current computational hardware… would quantum really reduce that amount by a significant enough margin?
I’m not so sure—but in this world it’s hard to tell VC hype from actual tech predictions.
So, you want an Apple AirTag, but you want to save a few bucks? Well maybe don’t trust Life360’s Tile to do the job. According to the Verge, Tile tags not only fail to implement common sense encryption, but they come with a so-called “anti-theft” mode that turns off the tag’s detectability… defeating the whole point of the tag in the first place.
Remember the 2008 bail-outs? Yesterday we looked at the story of Jaguar Land Rover starting to recover from their massive Cyber Attack. Via SecurityWeek this morning, we see that the UK government is giving a $2 billion loan guarantee to JLR’s creditor.
Will the bailout solve the problem, or just offer more incentive for bad actors to target UK institutions?
Coffee Break // Cyber News 004
Another Monday, another practice exam…
Gooood morning, ladies and germs,
Happy Monday! I hope everyone had a restful weekend. I had a grand old time getting caught up on sleep, catching up with my online RPG group.
I’m off to the races this morning with a little joe and a Sec+ practice exam. I got an 89% on this go-around; a solid improvement over the 72% I scored on it a month ago. Feelsgoodman.
\\
News round-up.
This morning.
I see that the Department of War has released an overview for their new cybersecurity framework. Frameworks in the cybersecurity space often serve the role of checklists for professionals to follow.
They are jumping off points that need to be tailored to the needs of a specific organization, but still serve as a solid starting point. Without documentation like this, even the best cybersecurity professionals will forget crucial vulnerabilities and leave potential openings in the attack surface.
In the crime world, a reminder that not all cyber crime is ransomware. A group calling themselves Radiant (No relation to Radiant, I imagine) stole pictures and personal data from a large number of nursery children and their families, the BBC reports.
As someone who substitute teaches now and again, nurseries, schools, and after-school operations haven’t exactly encouraged me in terms of their information security. Still, there is only so much you can do—when you put yourself or your child in the public square, you have to have a certain expectation that even undesirables may gain access to your information. 🎵Hide yo kids…🎵
In the world of supply chain attacks, Jaguar Land Rover has announced a partial resumption of production after a prolonged cyber-attack forced them to halt operations in early September. While I couldn’t find the specifics of the hack or the group behind it, the Guardian quotes Anupam Singhal as saying that JLR used:
“…smart factories where everything is connected.”
I can tell you right now, this lack of segmentation may not have enabled the hack to happen period, but it certainly allowed the hackers to violate such a large portion of JLR’s operation. In short: JLR may have had all their eggs in one basket in the name of efficient production.
The interruption in production will have cost them hundreds of millions of dollars by now and strained the finances of the smaller businesses in their supply chain.
This past weekend.
Suspected Russian incursions continues to test NATO members with drones violating their airspace. Will this be discussed at the unusual meeting of military brass that Defense Secretary Pete Hegseth has arranged?
A few more details trickle out about the Collins Aerospace cyberattack I’ve been following this past week. Evidently the attacker’s were using the ransomware “Hardbit.” SecurityWeek.com’s article discusses multiple different hacker groups that may have been behind the attack.
Coffee Break // Cyber News 03
A massive DDoS attack stopped by Cloudflare. Microsoft cuts off service for Israeli cyber Unit 8200.
Good morning guys and girls, I hope everyone has made it to Friday sane and a little richer than on Monday.
First, a quick matter of housekeeping. You may notice that a comments section has been enabled at the foot of this blog. Please chime in and let me know your takes on things!
The comments section of a given post should accept new comments for up to about a month after a post goes live. If you run into any issues with the comments section, please contact me through a different communication channel.
My security training trundles along this week with a focus on memorizing port numbers (some of the important ones, at least) and filling gaps in my knowledge. At this point I have a fairly good idea of what topics will be on the exam, and am methodically learning the ones that I can’t readily explain.
Practicing mastery of a topic by explaining it out loud is a process I’ve heard called the “Rubber Duck Method.” I endorse it fully—for me the most natural way to mentally manipulate a subject is to yap about it.
//
In the news.
A record setting UDP carpet bombing was mitigated by Cloudflare. The DDoS attack in question sent a whopping 11.5 Terabits per second (Tbps) for nearly a minute.
To put that in perspective, streaming an HD video from Netflix would take maybe as much as 7 Mbps. This attack was like 1.64 million devices trying to send video all at once to a single endpoint.
In international news, China is sanctioning U.S. companies that support Taiwan’s military capabilities. The companies affected include satellite communications companies and unmanned aquatic vehicle manufacturers.
As per the Guardian, Microsoft has terminated it’s contract with the Israeli military’s famous Unit 8200. Evidently Israeli forces were utilizing Microsoft’s Azure cloud service to store millions of Palestinian phone calls that were being made each day in Gaza.
“We do not provide technology to facilitate mass surveillance of civilians. We have applied this principle in every country around the world, and we have insisted on it repeatedly for more than two decades.”
—Brad Smith, Microsoft vice-chair and presidentFinally today, we have a report that at least one unspecified U.S. government agency was breached by a threat actor with suspected ties to the Chinese state. The hackers have evidently been exploiting the flaws for months. Yikes.
Coffee Break // Cyber News 002
As I study for the Sec+ exam, I ponder: are US companies selling spyware to China?
49 days until I take my Sec+ exam, and another 4 after that until I ship to BCT. In the meanwhile, I spend my days balancing study (shout out to Professor Messer), a little freelance graphic design and editing, and a few days of substitute teaching here and there to fill in the gaps.
Life is good, as is this lungo. (Which refers to the coffee, and not the slow-witted minion of remarkable strength that I keep in my employ…)
Studying is all well and good, as the materials that CompTIA and Prof. Messer put out are fairly comprehensive. Still, many gaps remain in my knowledge, and I find my head swimming by the afternoon as I attempt to memorize port numbers (I’ll come up with mnemonics for this dross if it kills me), attack vectors, and the countless acronyms that seem to infect the world of cyber.
I find that I have a fairly good grasp of all the surface level concepts, but struggle with the specifics of many areas, especially those that are focused around corporate conventions. My great disadvantage in this field is my lack of professional experience, which is something that I hope to remedy with my service in the National Guard, and my own futile attempts on homelabbing (more on that some other day.)
In the meantime I finish my coffee, and turn a passing eye to the news…
Following up on the stories that I’ve been tracking this week, we see more news sources reporting on the NY SIM farm. As more opinions chime in, I hear few voices echoing Marcus Hutchens’ skepticism. I’ll keep an eye on this on for a little while longer, but I suspect we may not receive any new developments.
In a development for the EU airport ransomware story, an unnamed man was arrested and subsequently released on bail in the UK. It will be interesting to see what, if anything, he’s charged and tried for.
In the surveillance space, more light is being shed on the role of American companies in aiding and abetting Chinese surveillance. Bipartisan voices are giving lip service to an important issue thats closer to home than some of them realize. Here in America, companies like Flock and Palantir increasingly provide the government with dangerously powerful surveillance infrastructure to capture and interrogate the data of private citizens.
Consider the recent reports of ICE using Stingrays to locate immigrants. I discussed this invasion of privacy with a family member recently, and was surprised when they expressed unequivocal support for the effort. This is a mistake. Even if you agree with the goal of a given organization (like ICE) the methods are problematic. A government agency trawling our neighborhoods and intercepting all of our communications is hugely problematic.
Imagine if an ICE van followed your mail delivery fan, and searched your letters as they were delivered. Is it any less of a violation of the 4th amendment that they are doing that to your unencrypted phone traffic? I need more coffee…
Coffee Break // Cyber News 001
Did we underestimate or overestimate the impact of the NYC SIM farm? Coverage from NPR clashes with that of cyber experts.
Good morning ladies and germs,
The world is still turning and burning (much like this cup of half-caf as it sears my stomach) and cyberspace is as always alight with warfare and crime. Here’s a quick round-up of some of this week’s cyber news so far.
Yesterday I covered the Secret Service’s press release about the SIM farm they busted near NYC. Major outlets have been picking up the story and adding their own spin to it over the past 24 hours and, much like I did at first, they’re largely parroting the Secret Service’s PR line. (More on that in a moment.)
Take, for example, NPR’s coverage of the matter. Not only do they repeat everything we learned in the original release, but they go on to imply that a PRC-linked APT group, (APT in this context refers to an Advanced Persistent Threat.) Salt Typhoon, might be involved. As far as I can tell however, this is pure speculation on NPR’s part.
But before we go wild with interest over the potential involvement of foreign governments, we should take a step back and examine the actual scope of the SIM farm in question.
Playing counter-point to the main stream media opinions is cyber analyst Marcus Hutchins. An expert known for helping counter the infamous WannaCry attack in 2017, Marcus emphasized the scale of the attack as a reason for tempering our alarm.
”New York is incredibly dense,” Marcus opines. “… Think about the New Year’s Eve ball drop—you have possibly a million or more people all in Times Square at the same time. That is way more cell phones than this device actually has. … So it’s unlikely that a device with this low capacity would actually be able to overwhelm New York’s cell network.”
This is a great reminder for how media coverage can spin a story. I, and I’m sure many others, listened to the initial coverage and thought “wow, 100,000 is such a big number… that must make a huge difference!” without really stopping to consider the context in which that number is put. As Hutchins pointed out, 100,000 SIMs is a drop in the bucket to the overall network of NYC.
In other news, ransomware attacks committed against EU airports last Friday continue to cause delays and interfere with business operations.
In recent years, ransomware has rapidly become the most lucrative scheme in organized cybercriminals’ playbooks. So much of our modern world is dependent on digital infrastructure that any interruption to these services can put businesses in the unenviable position of having to either pay off the ransom to decrypt their systems, or risk greater losses in business while the systems remain inaccessible.
Coffee Break // Cyber News 000
Secret Service seizes 100,000 SIM cards.
As I sip my espresso this morning (ok, fine—slurp.) my eyeballs roam over a secret service press release that a family member passed along.
Given my interest in electronic and wireless security, I’m eager to learn more.
The press release details how bad actors (criminal and foreign actors) in the NY Tri-state area had constructed a network of 300 SIM servers and 100,000 SIM cards across multiple sites in a 35 mile radius.
Special Agent in Charge Matt McMcool lays out the severity of this threat in his coverage on the Secret Services YouTube channel. This network had the capacity to take down cell phone towers and conduct major DoS attacks. Given the proximity of the network to UN General Assembly and it’s capacity to seriously disrupt the telecommunications infrastructure, one can understand why the Secret Service acted to take it down.
For me, stories like this highlight the reality of cyberwarfare in our IT infrastructure. At all times, our adversaries are scoping out both governmental (UN, US Gov, etc) and civilian systems to exploit.
So much of our daily lives are linked inextricably to the continuous operation of telecommunications networks.
Consider the impact of CrowdStrike going down from a bad update in July of last year, or the Russian virus NotPetya wiping out hundreds of millions of dollars of business by catching shipping giant Maersk in the crossfire of their cyberwar with Ukraine. How many 1s and 0s stand between you and your grocery store shutting down, and your gas stations running out?
I’ll try and follow this story a bit, and update it and others as time goes on.
Who do you think is behind this network that they’ve taken down?